sgID Login
To enable sgID Login, set the environment variable NEXT_PUBLIC_ENABLE_SGID to true.
When sgID log in is enabled, the log in page will have an additional SGID log in button.
By default, sgID login uses POCDEX to retrieve the user's government email. This makes it so that only government officers can log in to the application. If you would like to allow non-government officers to log in to the application, use the myinfo.email scope instead, and update the application code to use the email from MyInfo instead of POCDEX.
sgID setup
Check out the full sgID documentation here.
To set up SGID, follow the steps below:
Go to the sgID Developer Portal and log in with the Singpass mobile app.
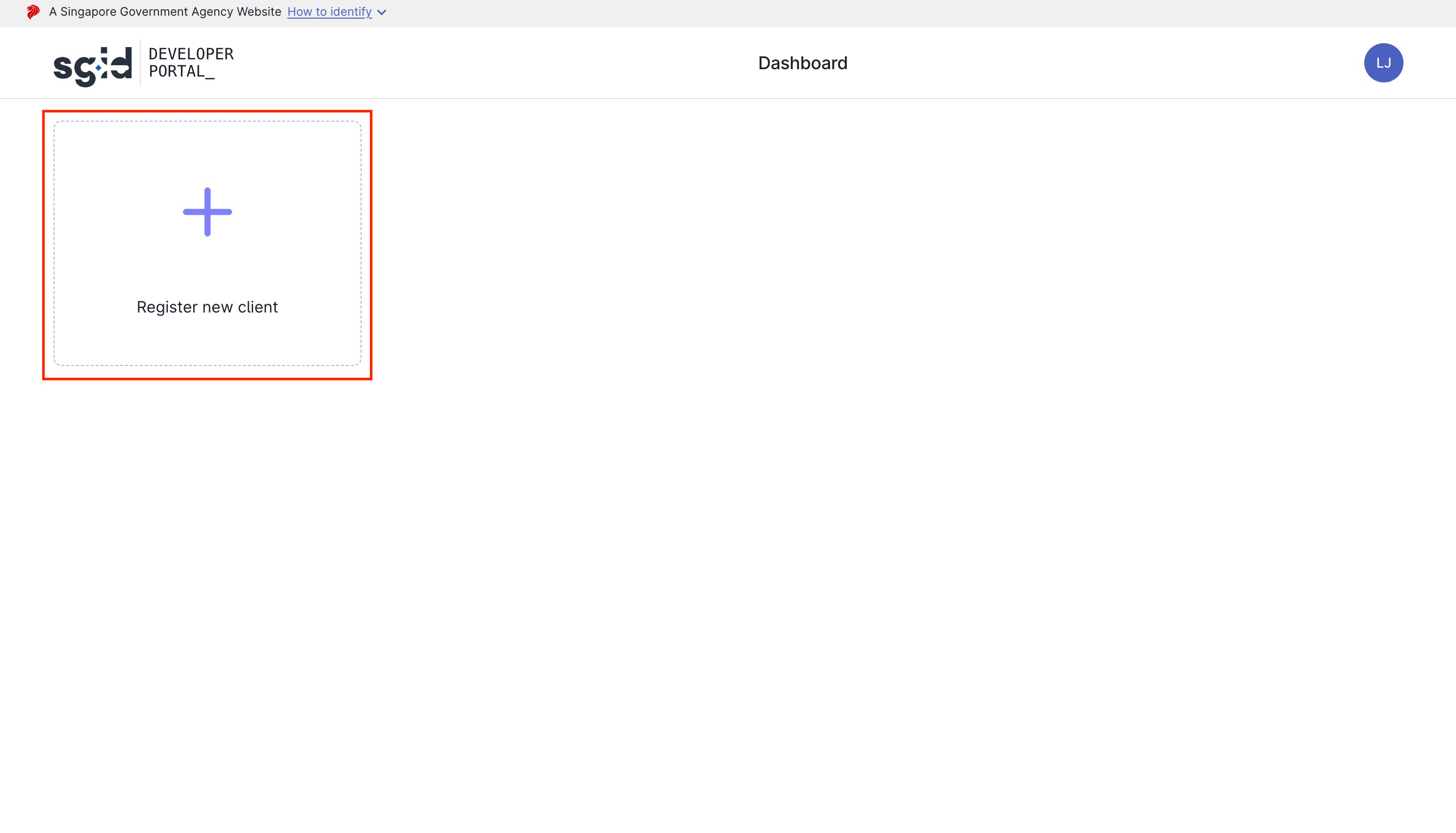
Register a new client by clicking on the "Register new client" button.
Fill in the following details of your application.
infoThe following values are for demonstration purposes only, please fill in the actual values for your application.
The SGID scopes
openid myinfo.name pocdex.public_officer_detailsis required for the Starter Kit to work. If you are to request for more scopes, check out the extending SGID scope section below.Redirect URLs have been set up in the application to be postfixed with
/sign-in/sgid/callbackdue to client side redirection. When adding your own redirect URL, ensure that it is postfixed with that path.Field Description Value Name Your client display name.
This will be displayed to the end user when they are logging in to your app with the Singpass mobile app.Starter KitDescription A brief description of the purpose of your client application.
This will be displayed to the end user when they are logging in to your app with the Singpass mobile app.This is to allow logging in with sgID on Starter KitScopes The maximum list of scopes that your app will be authorized to access. Please refer to the Data Catalog for the full list of scopes offered by sgID. openid myinfo.name pocdex.public_officer_detailsRedirect URLs The redirect URLs that sgID will be allowed to redirect to after the end user authenticates with the Singpass mobile app.
This should be the endpoint of your own application. You may need to add URLs on an adhoc basis for testing on generated URLs on Vercel preview deployments.http://localhost:3000/sign-in/sgid/callbackDownload the client credentials
cautionThe client secret is only shown once. Please download the client credentials and store them securely.
After completing registration, your client credentials will be generated. Download these credentials and store them in a safe place.

From the generated credentials, set the following environment variables accordingly. The variable keys should match the generated keys exactly:
SGID_CLIENT_IDSGID_CLIENT_SECRETSGID_PRIVATE_KEYSGID_REDIRECT_URI: This should be the same as the redirect URL you have set up in the sgID Developer Portal.
Extending sgID scope
The default scopes (openid myinfo.name pocdex.public_officer_details) are also set up in the application to be passed into the sgID SDK.
If you increase the scope requested, you will need to update the exported SgidUserInfo type in src/server/modules/auth/sgid/sgid.utils.ts to fit the new scopes.
You will also need to remember to update the APP_SGID_SCOPE in lib/sgid.ts or wherever the sgID SDK is used.